Phishing is when suspicious links are embedded in email messages, texts, or websites that might look legitimate at first glance. Those behind the attacks hope you will take the bait and click so they can try illegal tactics to steal your information.
Want to know if the University of Illinois really sent you that email?
Call the Information Technology Services Help Desk at 217-206-6000 and ask!
Don't Get Hooked
What is Phishing?
Phishing is a technique identity thieves use to steal your personal information, usually passwords or financial information. Like a fisherman using a lure to hook a fish, identity thieves try to lure you into giving up personal information by making what looks like a legitimate request from an organization you trust. These might look like they are from a bank, credit card company, or even the University. Unfortunately, phishing scams can be highly effective.
Common Phishing Types
Phishing
- Hackers impersonate a real organization or person to obtain your login credentials. You may receive an e-mail asking you to verify your account details with a link that takes you to an imposter login screen that delivers your information directly to the attackers.
Spear Phishing
- Spear phishing is a more sophisticated phishing attack that includes customized information that makes the attacker seem like a legitimate source. They may use your name and phone number and refer to the University in the email to trick you into thinking they have a connection to you, making you more likely to click a link or attachment that they provide.
Whaling
- Whaling is a popular ploy aimed at getting you to transfer money or send sensitive information to an attacker via email by impersonating a real University employee. Using a fake domain that appears similar to ours, they look like normal emails from a high-level official, typically the President, Chancellor, Provost, Dean or CFO, and ask you for sensitive information (including usernames and passwords).
Shared Document Phishing
- You may receive an email that appears to come from a file-sharing sites such as Box, Dropbox, or Google Drive alerting you that a document has been shared with you. The link provided in these emails will take you to a fake login page that mimics the real login page and will steal your account credentials
Vishing
- Vishing (voice phishing) is a form of criminal fraud conducted over the phone. The personal connection can make vishing attacks seem more believable. Cybercriminals typically try to get you to provide private personal and financial information. They also use vishing calls to gather information about an organization and its employees to reap financial rewards.
To avoid being phished, follow these guidelines
- Keep your password private.
- Only click on or download email attachments from people or companies you know.
- Don't click on unfamiliar links. Visit official company websites by typing their URL (website address) directly into a browser.
- Read carefully. If an email has a lot of misspelled words and really bad grammar, it’s probably a scam.
- Strangers don’t send millions of dollars to random people (you) on the internet.
Dissecting a phishing email
Phishing can be easy to spot
Phishing emails are often completely out-of-the-blue emails that ask you to click on a link and enter your password, may have a lot of misspelled words, or want you to download an attached picture or document.
It’s probably a phishing scam if:
- The email is unexpected yet reads like you’ve been having an ongoing conversation.
- You remember when you purchased something or talked to someone. The scammer hopes you don’t remember.
- The email asks you to “update your account” by clicking on a form and entering your password, credit card number, or account number.
- Banks, stores, credit cards, and the University of Illinois will never ask you for sensitive information (passwords, account numbers, credit card numbers, etc.) over email.
- The sender’s email address is the name of a legitimate company + common email provider. Example: buseybank@hotmail.com
- Banks have their own domains. They don’t send emails from common email providers like @hotmail.com or @gmail.com.
- The email has a generic greeting like “Dear User” or “Dear Most Honorable Friend and Confidante.”
- Legitimate companies personalize their greetings to their customers.
- There are misspelled words and bad grammar.
- Scammers tend to be lazy. They don’t take time to proofread.
- A few words are turned into a link instead of a long web address.
- Hover your cursor over the link without clicking it to see where it’s really taking you, or even more secure, visit the company site directly and find the information you seek.
How to Respond
Use the ProofPoint Report Spam Outlook Plugin to report spam to Security in a new and expanded fashion. Refer to the "Email, Using the Report Spam Outlook Add-in" knowledge base article to learn how to use the tool.
What does phishing look like?
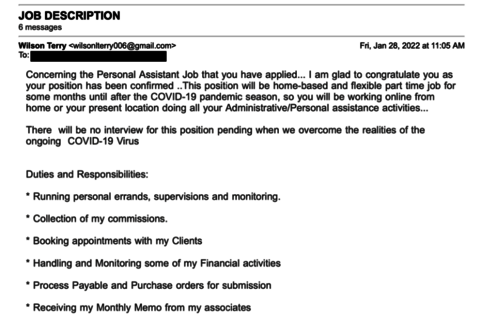
2022 has seen a large increase in phishing attempts targeting universities. A number of the campaigns have centered around job opportunities.
Proofpoint, the university's contracted vendor for online cybersecurity training, tracks these outbreaks and provided the following information.
- An employment fraud threat involves an attempt to recruit someone under the premise of a legitimate job offer. Threat actors will craft fraudulent job offers, hoping to steal money or personal information, or to recruit an individual to unknowingly comply with illegal activities such as money laundering. Threat actors will typically pose as recruiters or employers and try to entice victims with a variety of opportunities.
- A new variation of this scam involves a fake executive personal assistant position with the United Nations Children’s Fund (UNICEF). Spoofed or compromised university email addresses were used to send fake recruitment emails with links to a Google form. Posing as an applicant, a Proofpoint researcher completed the form. The attacker responded, claiming that the “applicant” had been chosen despite no interview taking place, attributing this to “the realities of the ongoing COVID-19 Virus.”
